Whether you work for a large business company or government institution, your data is crucial. With the increasing number of data breach cases, it’s evident that any company can fall prey to data hijacking and security breaches irrespective of its industry type.
Going by the numbers, cyber crime now makes up for a massive 40% of all recorded security-related incidents. In terms of money, the average cost of data breach hit an exuberant £3.2 million (approximately $4.18 million) and things aren’t getting any better.
In fact, almost 90% of CIOs and IT professionals admitted that data security is their top priority. That said, out of those surveyed only 21% were confident of the collaborative security systems and solutions being used in their companies. What is to be learned from the above information?
The takeaway from the above statistics is to start putting cyber security on top of your list. Cybersecurity is already a known concept in the software development world. Maybe project managers aren’t aware of it as much as they should and that’s why they are most susceptible of being attacked by these malicious criminals.
Thus, in the wake of increasing attacks, the number of organizations emphasizing the importance of data security is rapidly increasing. Also, they are willing to educate employees about the basics of collaborative security so they aren’t in any danger of being left behind and handle threats better.
Here are some basics of cyber security every project manager should know:

Protect data at all times
With every new project comes new data to take care of. Mind you, this data needs to be well-protected along with being managed well. Thus, project managers need to be mindful of the value of the data they are working with. While working with contracts and payroll, employ enough security measures.
Data encryption is one of the most reliable methods of data protection. It changes the text into a coded form so that nobody can access it unethically. Even if it does, data hackers can’t convert it to a readable form.
Strong passwords
In one of the studies, it is found that most of the breaches held in the last few years had weak passwords. If you’re likely to lead a team or project in the future, don’t forget to secure your email address with a strong password.
Setting up strong passwords is also one of the easiest ways to secure sensitive information from unwanted people. Failing to do so will enable hackers to access your login credentials, guess your password, and steal important information from your business network.
Two-factor authentication (2 FA)
Along with secured passwords, add two-factor authentication to your login accounts helping only authorized users to access them. It is an extra layer of security used to make sure the right person gains access rights to the account.
In this process, a user has to enter his username and password. Then a code is sent separately to a connected mobile device. Alternatively, another piece of information can be anything from a personal identification pin (PIN), secret questions, or credit card information, and can even go to advanced security measures such as the biometric pattern of a fingerprint, iris scan, etc. Thus, two-factor authentication is quite effective in protecting your confidential project or business information from being exploited.
Communicate securely
Oftentimes, team members share confidential information through online chat or other social media platforms. After Facebook’s massive security breach, it is quite evident that companies and businesses are quite vulnerable to security attacks.
Thus, it’s essential to implement proper company security guidelines while planning for secure communication on a project. It will depend on the nature of the data being shared to integrate security preferences or not. We suggest you should. It’s your duty to make sure your team uses a reliable and secure communication tool like ProofHub helping them to communicate and share files with tight security without any hassle.
“Communicate as easily with remote team members as you would with your in-house team. Try ProofHub.”
Offer proper training (Live fire training)
Oftentimes, employees take unnecessary risks online putting the business security in danger. It pays well to offer proper training to your staff in the best cybersecurity practices as it might be the difference between safe data handling and a security breach. Don’t worry, it’s not as time-consuming as you think.
Make them aware of potential risks and their role when it comes to data security. Simulated cyber security attacks are effective training methods where phishing attacks are set up by the IT team to see how many people are susceptible to clicking on such emails. Such drills are the best way to coach employees on how to not fall for such traps.
This training will also help you understand how to use tools like ProofHub and other solutions against such intrusive attacks.
How ProofHub raises the bar of cyber security
We understand that data security is crucial to you. ProofHub team works very hard to keep your data secure, safe, and private. We are continuously engaged to provide great care to protect your data and keep updating security from time to time.
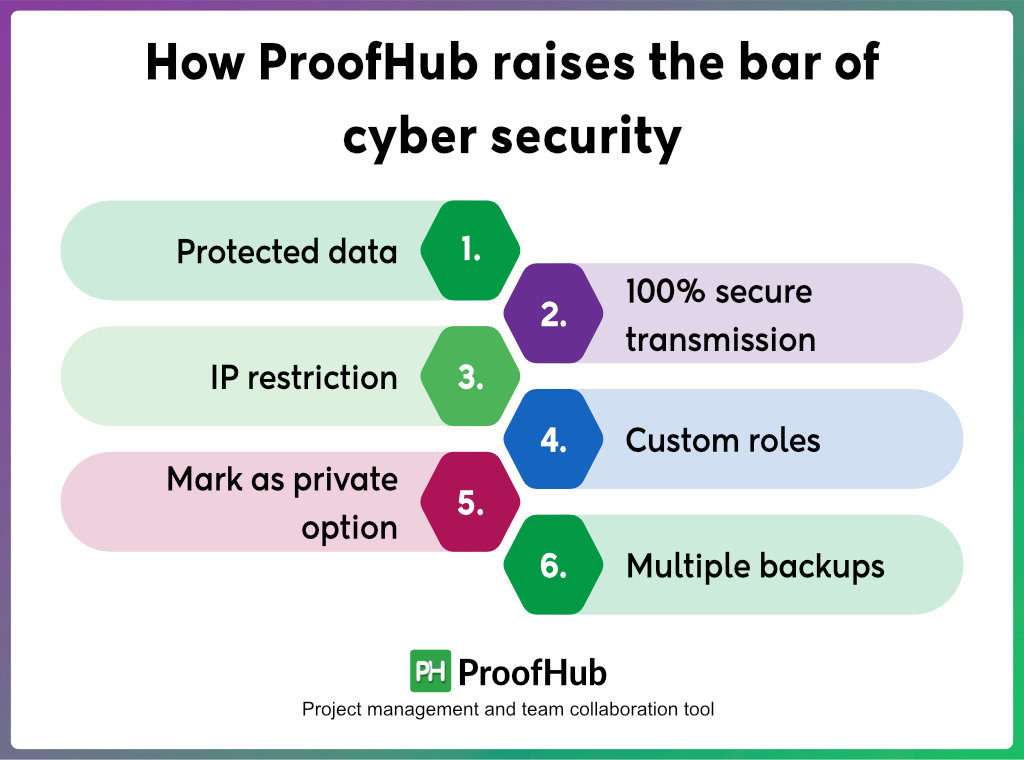
Our latest collaborative security features include:
Protected data
Along with dynamic solutions, ProofHub believes in keeping customer’s data secure and safe. Our strict security policy makes sure how data is accessed, stored, shared, and protected both within and outside the tool. Your data is stored in reliable servers and also in multiple places employing modern techniques so it can be easily retrieved in case of failure.
100% secure transmission
We offer the highest level of security often used by banks to protect your data. Whenever you enter sensitive information in ProofHub and it reaches to our data centers, we encrypt the transmission of that data using Secure Socket Layer (SSL) technology.
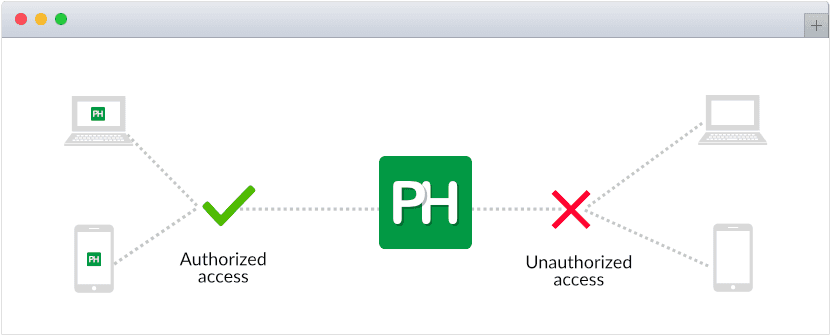
IP restriction
In ProofHub, you can restrict your account access to only those IP addresses that you select and avoid unauthorized access to keep your data secure. IP restriction lets you boost security and get ultimate control over your account without unwanted restrictions.
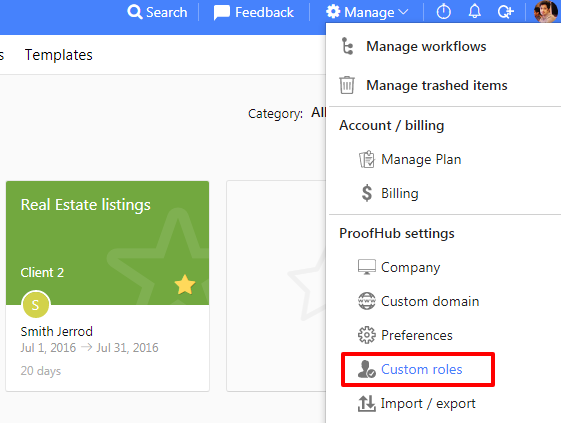
Custom roles
Create custom access roles and choose who does, sees, and manages what. Provide permissions and grant access privileges to choose what you want each user to view, add, and manage in ProofHub.
Note: Many tools are offering advanced user access controls in their Enterprise or Pro plans but you get to try and test Custom Roles, Network Control, and API access for free in ProofHub.
“Want to keep your project information safe and secure? Switch to ProofHub.”
Mark it as the private option
ProofHub gives you the option to mark tasks, discussions, notes, and timesheets as private which means only those assigned can access them to make sure the information goes into the right hands keeping no room for data theft.
Multiple backups
ProofHub runs over the most trusted communication protocols on the internet such as SSL/HTTPS. It backs up the data on an hourly basis and data copies are saved and secured at an off-site location for disaster recovery.
All in all, ProofHub makes it easier and more intuitive for its users to manage sharing settings enabling them to get the ultimate control over projects and visibility.
Start taking cyber security seriously
In today’s digital world, it’s important to be responsible for the data you share with others. It’s everyone’s responsibility to be equally invested in maintaining the security of your project whether it’s a large company or a relatively smaller one. Start implementing enough security measures in every project phase during the lifecycle of your project.
ProofHub’s 100% secure transmission, IP restriction, custom roles, and other advanced security features make us a reliable and secure collaborative work management solution among others.
To learn more about ProofHub’s security practices, do visit our security page.

